Last Updated 6 Jan 2019
This is the third in a series of security challenges.
These are designed to show ways of making Access apps reasonably secure.
1. The application is an ACCDE file so all VBA code has been removed.
The file has been renamed as a runtime file (ACCDR). It will not run if the file type is changed.
2. Startup properties have been modified e.g. shift bypass disabled. It will not run if this is re-enabled
There is no access to the navigation pane, ribbon, options menu or the rest of the application window
The taskbar and all desktop items are also removed. These are restored automatically when the
application is closed using the Quit button
3. Mouse movement is confined within the active form
4. The app is password protected and the password is NoDBG. It will not run if this is altered or removed
5. No changes are made to your computer by running this app. There are no restrictions on the number of
times it can be run
The challenge is intended to be solvable.
Solving it will require some different methods to those used in the previous challenges
Once again the app includes 'special tables' - both read only and deep hidden
The app contains 3 forms - the first form is shown in the screenshot
At first the Click Me button will be disabled, locked and hidden.

The other 2 forms CANNOT be opened directly
The main parts of the challenge are to:
a) find out how to show/enable/unlock the Click Me button on the main form
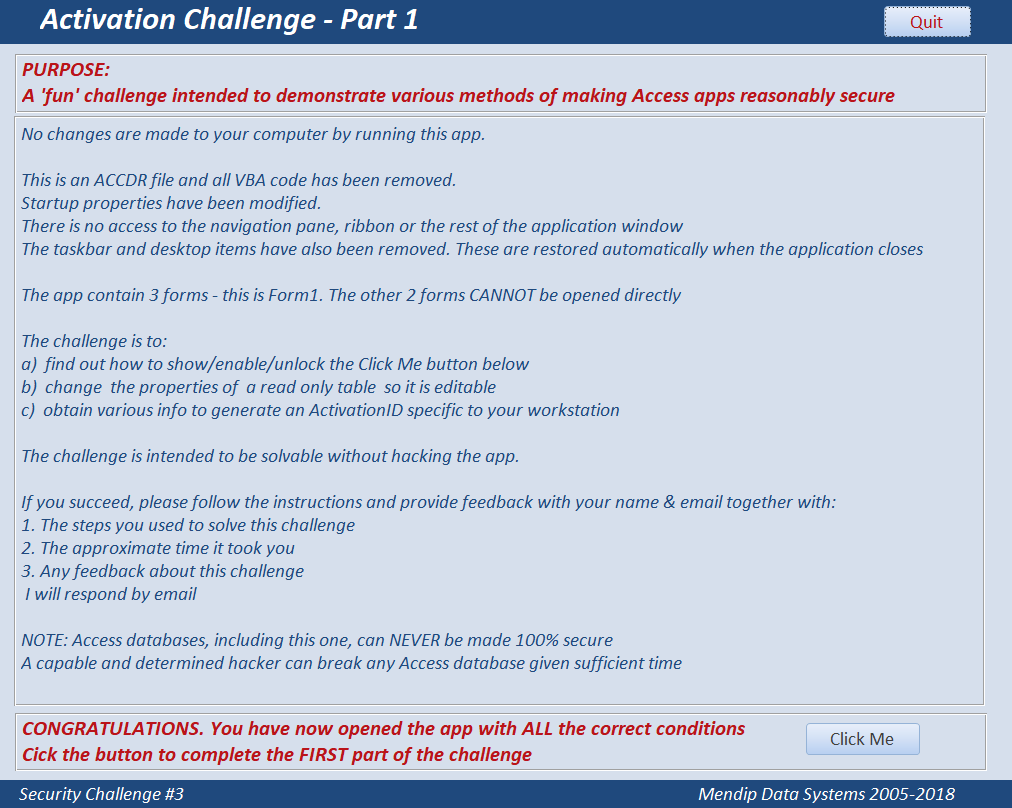
b) change the properties of a read only table and modify its contents
c) use VBA functions to obtain various info and use this to generate an ActivationID specific to your workstation
The challenge is intended to be solvable without hacking.
Indeed trying to hack it will probably make it harder to solve.
Follow the clues provided in this thread and the challenge itself.
HINT: Solving this may be easier on certain computer systems. Hence difficulty level = 3.5 stars overall
You may need to search online for solutions to certain parts of the challenge
I hope you enjoy puzzling out this challenge.
If you succeed, please follow the supplied instructions to provide feedback by sending an email using the feedback form provided.
Please include the answers to a, b & c together with how you solved the challenge and the approximate time taken. Screenshots may be useful
NOTE:
Access databases, including this one, can NEVER be made 100% secure
A capable and determined hacker can break any Access database given sufficient time
Both 32-bit & 64-bit versions have been supplied
Click to download the correct version for your computer:
Activation Challenge (32-bit) ; Activation Challenge (64-bit) Approx 1.3 MB (zipped)

Feedback
Please use the contact form below to let me know whether you found this article interesting/useful or if you have any questions/comments.
Do let me know if you find any bugs in the application.
Please also consider making a donation towards the costs of maintaining this website. Thank you
Colin Riddington Mendip Data Systems Last Updated 14 Mar 2019

|
Return to Security Challenges Page
|
Return to Top
|