
First Published 24 Oct 2023 Last updated 6 Nov 2023
Back in March 2022, I wrote an article, Adding Security to Access Databases - A Wish List
The article listed 11 security weaknesses that in my opinion should be addressed to make Access files more secure.
Before publishing the article, I had submitted a request to the Access team for each of these items to be fixed in a future Access update, at least for ACCDE files.
Sadly, over 18 months later, there is still no indication of any of these feature requests being implemented.
This article discusses the first of those security weaknesses in more detail and explains why it is important.

The Problem
When an Access developer is building a split database, it is very useful to view the connection details for linked backend Access/SQL Server tables.
However, once a front-end application is distributed as an ACCDE file, there is absolutely no reason for end users to be able to view those connection details.
Indeed, allowing this to happen makes the backend database much less secure
However, it is far too easy for end users to do so.
When ACCDE files are distributed, the navigaton pane should normally be hidden to end users.
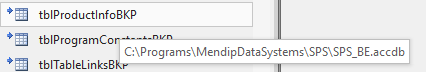
Where users can view the details of linked tables in the navigation pane, connection string details can be viewed by hovering over any linked table. For example:
Linked Access table:
Linked SQL Server table:
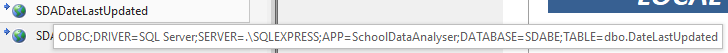
Whilst the connection string is visible, the password is not shown. So far, so good!
Next we can right click on any linked table and select Linked Table Manager
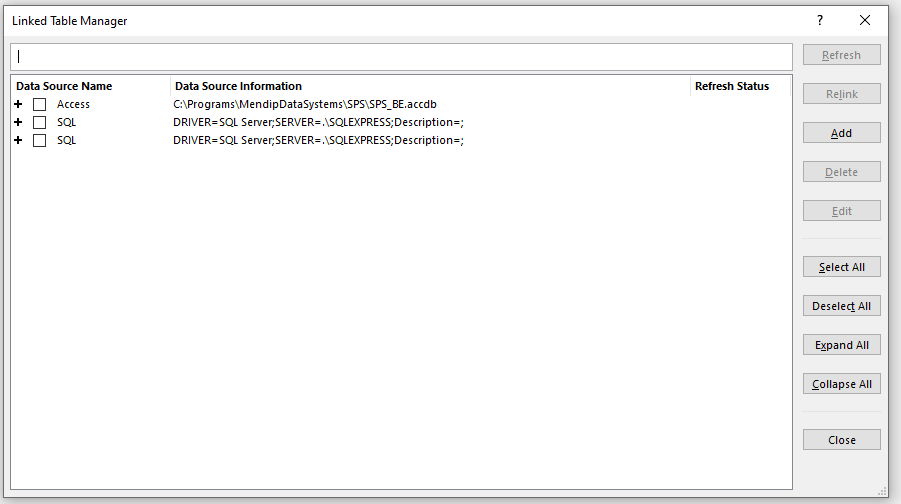
Select one of the linked table data sources and select edit to view the connection details
Linked Access table:
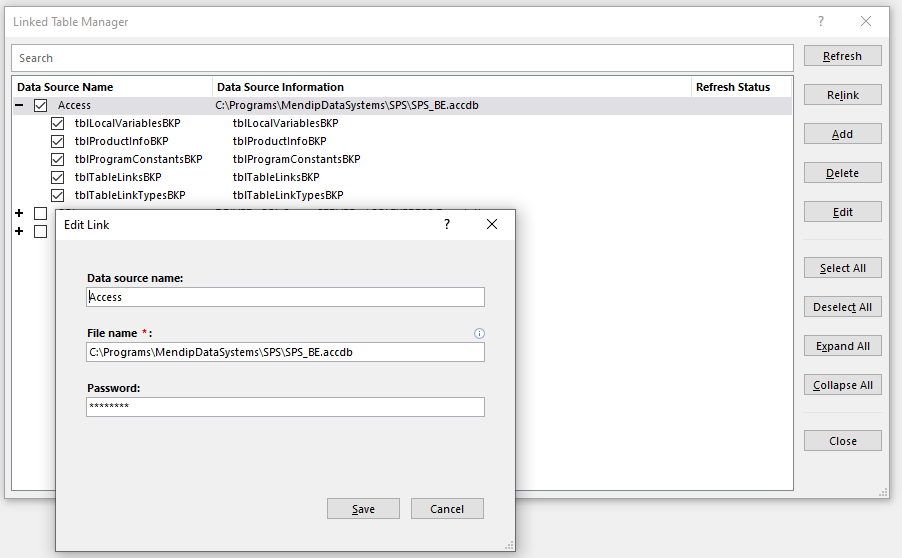
Here the password is masked.
Linked SQL Server table:
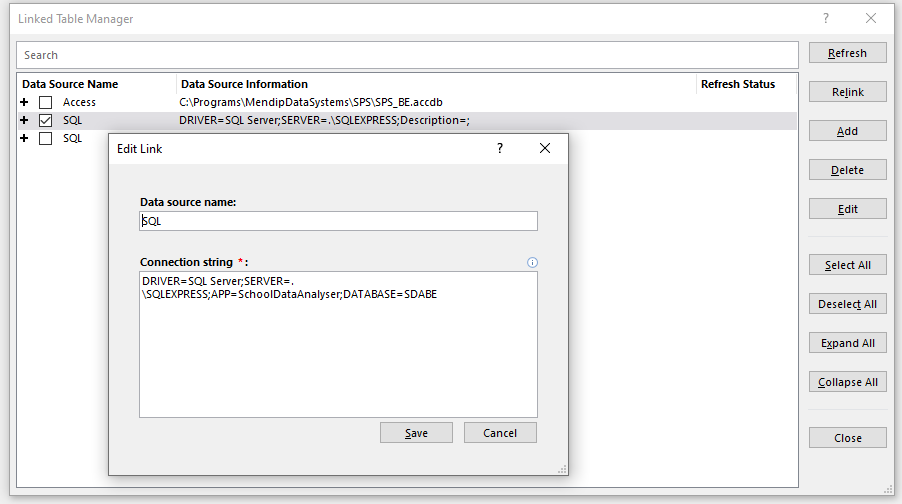
In this case, the password is not shown
Again, so far, all is fine!
However, the hidden MSysObjects system table can easily be made visible by end users.
Doing this immediately exposes the entire connection string for all backend tables in the Connect field.
If the connection string contains a password this will be shown without a mask.
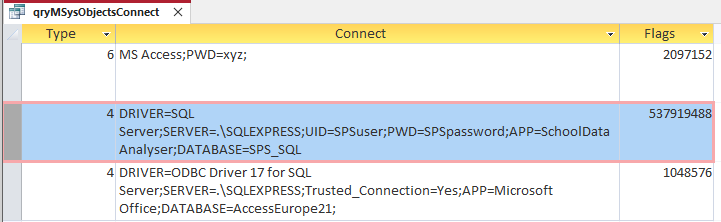
This means the password is shown for all linked Access tables in password protected databases.
For ODBC databases such as SQL Server and Azure SQL, different types of connection are available.
Trusted connections do not have a password in the connection string.
For users running Access runtime, additional security is enforced and the above methods do not work.
Many developers simulate runtime mode by saving files as ACCDE and renaming as ACCDR.
However, anyone with moderate Access knowledge knows that change can be reversed
It also also possible to view the MSysObjects table in an ACCDR file from an external database.
Although doing this isn't difficult, I am deliberately NOT going to assist anyone trying to hack a database by explaining how it can be done.

Proposed Solutions
1. One solution to this security weakness is very simple:
Mask passwords in the MSysObjects table of ACCDE/ACCDR files
However, doing this may be considered impractical for backwards compatibility, in case it breaks functionality in some existing databases.
2. An alternative would be to create a new more secure version of the ACCDE file type e.g. ACCDS where passwords are masked.
If this was done, other security improvements could also be included. More details in a future post!
If you would like to see this issue addressed, please vote for my suggestions in the Microsoft Feedback portal

Feedback
Please use the contact form below to let me know whether you found this article interesting/useful or if you have any questions/comments.
Please also consider making a donation towards the costs of maintaining this website. Thank you
Colin Riddington Mendip Data Systems Last updated 6 Nov 2023

Return to Access Blog Page
Return to Top